Phishing attacks steal consumers’ personal identity data and financial account credentials. Phishers use ‘spoofed’ e-mails to lead consumers to counterfeit websites designed to trick recipients into divulging financial data such as credit card numbers, account usernames, passwords and social security numbers.
Hijacking brand names of banks, e-retailers and credit card companies, phishers often convince recipients to respond. Pharming crimeware misdirects users to fraudulent sites or proxy servers, typically through DNS hijacking or poisoning.
The term phishing comes from the fact that Internet scammers are using increasingly sophisticated lures as they “fish” for users’ financial information and password data.
Phishers may use an address containing the “@” symbol, for example http://[email protected]/. These addresses will attempt to connect as a user www.google.com to the server members.tripod.com. This will very likely succeed even if the user does not exist, and the first part of the link may look legitimate. The same is true for misspelled URLs or subdomains, for example http://www.yourfavbankdomain.com.spamdomain.net.
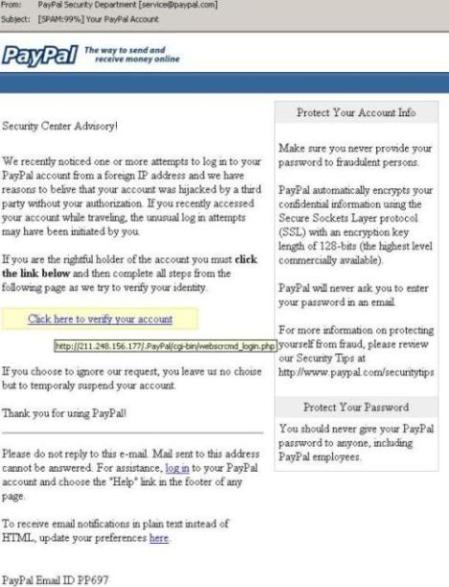
Here is an example of phishing using Paypal-kind-of email. Note that the link Click here to verify your account is actually linking to an IP address instead of the Paypal website. So, make sure that you never directly click on a link in the email to supply your personal information, especially for financial institutions. Go to their home page by typing the URL in the address bar and navigate to the page. That is safe.
Damage Caused by Phishing
The damage caused by phishing can be anything from not able to access your email to losing all the money in your bank account. All they need to do this is to have your personal information that you use for authentication purposes. When you reveal this to these phishing sites, they get your personal secret information and can handle it any way they want. They might even prevent you from accessing your own accounts.
It is estimated that between May 2004 and May 2005, approximately 1.2 million computer users in the United States suffered losses caused by phishing. The estimated total of the losses is approximately $929 million USD. Furthermore, U.S. businesses lose an estimated $2 billion USD a year as their clients become victims.
Anti-Phishing
The AntiPhishing Working Group (APWG) is a consortium that brings together businesses affected by phishing attacks, businesses that provide security products and law enforcement.
The APWG has over 500 members including leading security companies such as Symantec, McAffe and VeriSign.
Pharming
Pharming is the exploitation of a vulnerability in the DNS server software that allows a hacker to acquire the Domain Name for a site, and to redirect that website’s traffic to another web site.
As you know, every website on the Internet has a distinct IP Address. DNS servers map website domain name to IP address of the machine where the webpages are actually located. Pharmers attack the DNS servers and redirect a domain name to a different IP address where fake website is located. It is something like, a telephone exchange hacker redirecting your phone calls to a fake number. So all traffic to the domain name will be redirected to the fake website. This fake website, having the same look & feel of the original website, can be used to “phish” or steal a computer user’s passwords, PIN number or account number. This is only possible when the original site wasn’t SSL protected, or when the user is ignoring warnings about invalid server certificates.
Social Engineering
Social engineering is the practice of obtaining confidential information by manipulation of legitimate users. A social engineer will commonly use the telephone or Internet to trick people into revealing sensitive information or getting them to do something that is against typical policies. It is generally agreed upon that “users are the weak link” in security and this principle is what makes social engineering possible.
Useful Links


Be the first to comment